ɩɨɥɶɡɨɜɚɬɟɥɸ
B
ɫɨɨɛɳɟɧɢɟ ɨɬ ɩɨɥɶɡɨɜɚɬɟɥɹ
T
&
ɡɚɲɢɮɪɨɜɚɧɧɨɟ ɫ ɩɨɦɨ
'
ɳɶɸ ɤɥɸɱɚ ɩɨɥɶɡɨɜɚɬɟɥɹ
B
4
)
/
(
%
,
8
)
,
)
B
(
T, L, K,
%
)
.
Ɍɚɤɢɦ ɨɛɪɚɡɨɦ ɤɥɢɟɧɬ ɞɨɤɚɡɵɜɚɟɬ ɫɜɨɸ ɩɨɞɥɢɧɧɨɫɬɶ ɫɟɪɜɟɪɭ
&
ɩɨɥɭɱɚɟɬ
ɜ ɫɜɨɟ ɪɚɫɩɨɪɹɠɟɧɢɟ ɫɟɚɧɫɨɜɵɣ
"
ɫɟɫɫɢɨɧɧɵɣ
#
ɤɥɸɱ
&
ɤɨɬɨɪɵɣ ɨɧ ɦɨɠɟɬ
ɢɫɩɨɥɶɡɨɜɚɬɶ ɞɥɹ ɤɪɢɩɬɨɝɪɚɮɢɱɟɫɤɨɣ ɡɚɳɢɬɵ ɫɨɨɛɳɟɧɢɣ
&
ɩɟɪɟɞɚɜɚɟ
'
ɦɵɯ ɦɟɠɞɭ ɤɥɢɟɧɬɚɦɢ
(
.(
ȼ ɪɚɦɤɚɯ ɞɚɧɧɨɝɨ ɩɪɨɬɨɤɨɥɚ ɜɨɡɦɨɠɧɨ ɩɪɨɞɨɥɠɟɧɢɟ ɨɛɦɟɧɚ ɫɥɭ
'
ɠɟɛɧɵɦɢ ɫɨɨɛɳɟɧɢɹɦɢ ɜ ɫɥɭɱɚɟ
&
ɟɫɥɢ ɧɟɨɛɯɨɞɢɦɚ ɜɡɚɢɦɧɚɹ ɚɭɬɟɧɬɢ
'
ɮɢɤɚɰɢɹ ɤɥɢɟɧɬɨɜ
(
Ɉɫɨɛɟɧɧɨɫɬɶɸ ɞɚɧɧɨɝɨ ɩɪɨɬɨɤɨɥɚ ɹɜɥɹɟɬɫɹ ɠɟɫɬɤɚɹ ɫɢɧɯɪɨɧɢɡɚɰɢɹ
ɜɪɟɦɟɧɢ ɜɫɟɯ ɩɨɥɶɡɨɜɚɬɟɥɟɣ
"
ɤɥɢɟɧɬɨɜ ɢ ɫɟɪɜɟɪɨɜ
#
ɫɨ ɜɪɟɦɟɧɟɦ ɩɨɥɶ
'
ɡɨɜɚɬɟɥɹ
T
&
ɤɨɬɨɪɚɹ ɞɨɫɬɢɝɚɟɬɫɹ ɫɢɧɯɪɨɧɢɡɚɰɢɟɣ ɫ ɧɚɞɟɠɧɵɦ ɫɟɪɜɟɪɨɦ
ɜɪɟɦɟɧɢ ɫ ɬɨɱɧɨɫɬɶɸ ɞɨ ɧɟɫɤɨɥɶɤɢɯ ɦɢɧɭɬ
(
Ɏɭɧɤɰɢɨɧɚɥɶɧɵɟ ɨɫɨɛɟɧɧɨɫɬɢ ɩɪɨɬɨɤɨɥɚ
E_l\_lim
(
Ɏɭɧɤɰɢɨ
'
ɧɚɥɶɧɚɹ ɫɯɟɦɚ ɩɪɨɬɨɤɨɥɚ
E_l\_lim
ɨɬɧɨɫɢɬɟɥɶɧɨ ɩɪɨɫɬɚ
(
Ɉɧɚ ɩɨɞɪɚɡɭ
'
ɦɟɜɚɟɬ ɧɚɥɢɱɢɟ ɫɥɟɞɭɸɳɢɯ ɤɨɦɩɨɧɟɧɬɨɜ
"
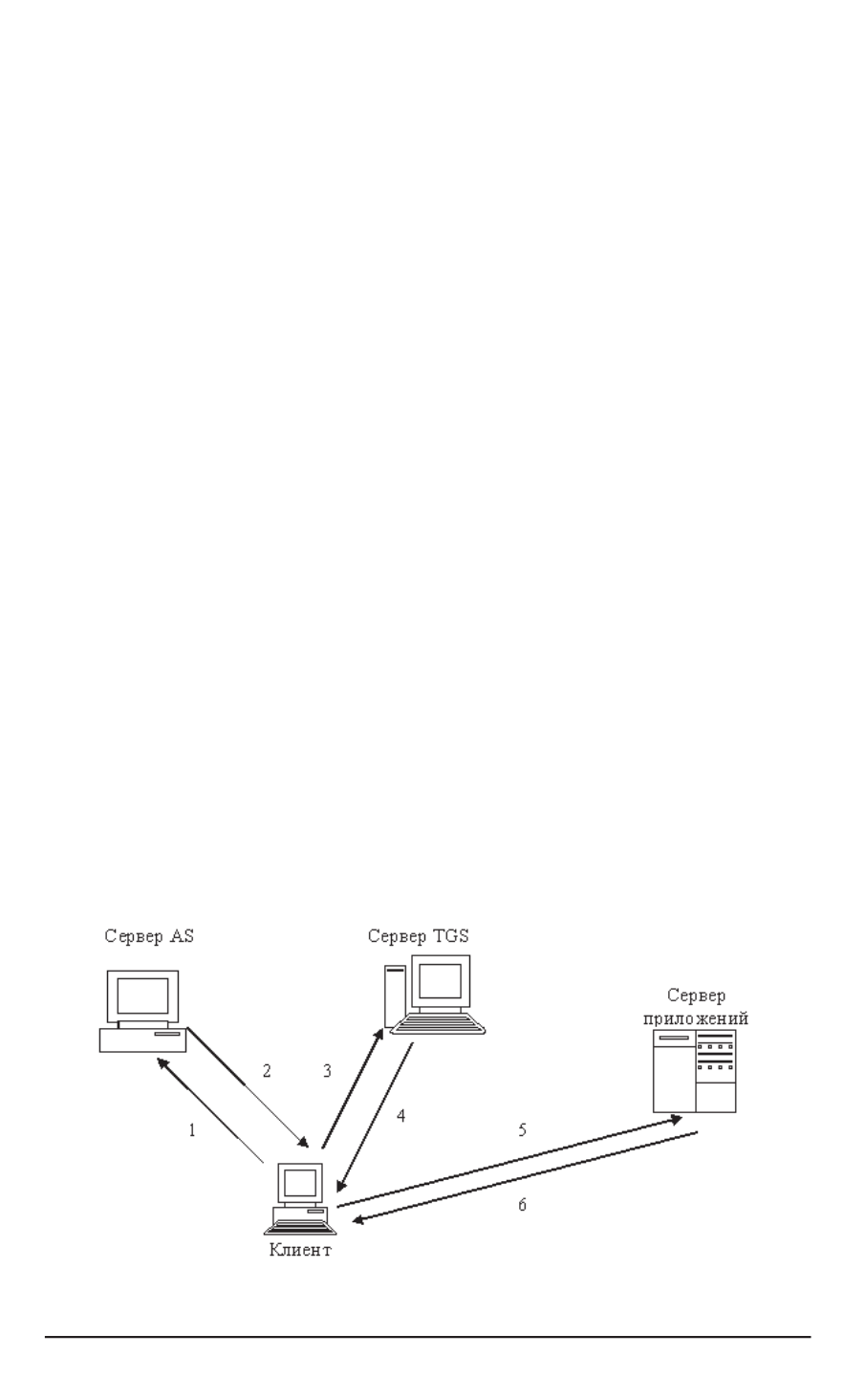
ɪɢɫ
( +#4
ɫɟɪɜɟɪɚ ɧɚɱɚɥɶɧɨɣ ɚɭɬɟɧɬɢɮɢɤɚɰɢɢ
5
ɫɟɪɜɟɪɚ ɜɵɞɚɱɢ ɛɢɥɟɬɨɜ
5
ɫɟɪɜɟɪɚ ɩɪɢɥɨɠɟɧɢɣ
&
ɩɨɞɞɟɪɠɢɜɚɸɳɟɝɨ ɩɪɨɬɨɤɨɥ
E_l\_lim5
ɤɥɢɟɧɬɚ
&
ɩɨɞɞɟɪɠɢɜɚɸɳɟɝɨ ɩɪɨɬɨɤɨɥ
E_l\_lim5
ɭɞɚɥɟɧɧɨɝɨ ɫɟɪɜɟɪɚ ɚɞɦɢɧɢɫɬɪɢɪɨɜɚɧɢɹ
"
ɤɨɬɨɪɵɣ ɧɟ ɹɜɥɹɟɬɫɹ
ɨɛɹɡɚɬɟɥɶɧɵɦ ɢ ɩɪɢɫɭɬɫɬɜɭɟɬ ɧɟ ɜɨ ɜɫɟɯ ɪɟɚɥɢɡɚɰɢɹɯ
#(
ɇɚ ɪɢɫ
( +
ɨɬɦɟɱɟɧ ɩɨɪɹɞɨɤ ɩɟɪɟɞɚɱɢ ɫɨɨɛɳɟɧɢɣ
"+0#(
ɉɪɨɬɨɤɨɥ ɫɟɬɟɜɨɣ ɚɭɬɟɧɬɢɮɢɤɚɰɢɢ
E_l\_lim
ɩɪɟɞɫɬɚɜɥɹɟɬ ɫɨɛɨɣ
ɧɚɛɨɪ ɫɭɛɩɪɨɬɨɤɨɥɨɜ
(
ɉɪɨɬɨɤɨɥɵ
&
ɢɫɩɨɥɶɡɭɟɦɵɟ ɫɢɫɬɟɦɨɣ
E_l\_lim&
ɩɪɟɞɫɬɚɜɥɟɧɵ ɧɚ ɪɢɫ
( ,(
Ɋɢɫ
( +(
Ɏɭɧɤɰɢɨɧɚɥɶɧɚɹ ɫɯɟɦɚ ɩɪɨɬɨɤɨɥɚ
E_l\_lim
/. CMMH *,-0'-3--(
ȼɟɫɬɧɢɤ ɆȽɌɍ ɢɦ
(
ɇ
(
ɗ
(
Ȼɚɭɦɚɧɚ
(
ɋɟɪ
(
ɉɪɢɛɨɪɨɫɬɪɨɟɧɢɟ
( ,**/(
ʋ
+


